PCI Compliance on Oracle Cloud Infrastructure is EASY!
Note: My original blog was published in ORACLE CLOUD INFRASTRUCTURE blog site on August 20th, 2018. I have republished it here with permission.
Official Disclaimer: The views and opinions expressed in this blog are those of the author and do not necessarily reflect the official policy or position of Oracle Corporation.
Oracle Cloud Infrastructure services have the PCI DSS Attestation of Compliance. The services covered are Compute, Networking, Load Balancing, Block Volumes, Object Storage, Archive Storage, File Storage, Data Transfer Service, Database, Exadata, Container Engine for Kubernetes, Container Registry, FastConnect, and Governance. In this blog post, we discuss the guidelines that help Oracle Cloud Infrastructure customers achieve PCI compliance for workloads running on Oracle IaaS.
Background
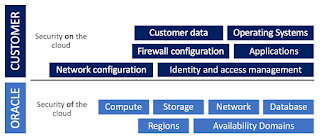
Our guidelines for achieving PCI compliance fall on the shared-responsibility spectrum of the cloud security continuum. The following diagram describes the separation between responsibility for the security "of" the cloud and security "on" the cloud.
As a customer, you are responsible for securing your workloads on Oracle Cloud Infrastructure. In some cases, you need to configure the services that Oracle provides. The responsibility is shared - Oracle maintains the services infrastructure and the customer consumes the services and configures the controls according to their security and compliance requirements. The following picture from the International Information System Security Certification Consortium (ISC2) clarifies the areas of responsibility for IaaS, PaaS, and SaaS:
We follow Oracle's 7 Pillars of Trusted Secure Enterprise Platform to develop solutions that meet the customer’s security and compliance requirements. We will discuss this more in our next blog post on Security Solutions Architecture. For now, let’s focus on PCI on Oracle Cloud Infrastructure.
Recommended High-Level Solutions for PCI Compliance on Oracle Cloud Infrastructure
We follow the latest official publication from PCI Security Standards Council (R) - Requirements and Security Assessment Procedures version 3.2.1 (May 2018). As per the document, there are 12 detailed requirements across 6 sections that cover how to:
Build and Maintain a Secure Network and System
Protect Cardholder Data
Maintain a Vulnerability Management Program
Implement Strong Access Control Measures
Regularly Monitor and Test Networks
Maintain an Information Security Policy
There are additional requirements for shared hosting providers like Oracle and we have already met the requirements through our attestation.
Let's dive into the solutions.
Section 1: Build and Maintain a Secure Network and System
Requirement 1: Install and maintain a firewall configuration to protect cardholder data.
Solution: Use Oracle Cloud Infrastructure security lists (Oracle Cloud Infrastructure managed subnet-specific firewall rules). In addition, download Fortinet or Checkpoint firewall images from our Marketplace and provision firewall appliances on Oracle Cloud Infrastructure.
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters.
Solution: Review the guidance in the PCI document. In addition, we have detailed documentation on how to manage user credentials on Oracle Cloud Infrastructure.
Section 2: Protect Cardholder Data
Requirement 3: Protect stored cardholder data.
Solution: This involves protecting data at rest. By default, Oracle Cloud Infrastructure Block and Object Storage are encrypted. Additionally, with our upcoming KMS, or any supported HSM, Oracle Wallet, Oracle Key Vault and third-party vault offerings, we give you unprecedented flexibility around key and secret management. For data security, we provide Transparent Data Encryption (TDE) and column level encryption.
Requirement 4: Encrypt transmission of cardholder data across open, public networks.
Solution: All our control and management plane communications are protected with TLS, which is necessary for the PCI DSS attestation. We also recommend using TLS (not SSL) and front-ending the application with our load balancers, as and when required. Use of SSH and IPSec VPN along with FastConnect is highly recommended.
Section 3: Maintain a Vulnerability Management Program
Requirement 5: Protect all systems against malware and regularly update antivirus software or programs.
Solution: Use our Dyn Malware Protection service to block malware at the edge of the your logical network before it can infect web applications running on Oracle Cloud Infrastructure. Additionally, ensure that anti-virus software is deployed at the OS level.
Requirement 6: Develop and maintain secure systems and applications.
Solution: We have many recommendations to develop and maintain secure systems. Have a patch management policy in place and use a managed cloud service provider for this purpose. If you're looking for a managed cloud service provider, Oracle Managed Cloud Services is an option along with many of our Oracle Cloud Infrastructure MSP partners.
Section 4: Implement Strong Access Control Measures
Requirement 7: Restrict access to cardholder data by business need-to-know.
Requirement 8: Identify and authenticate access to system components.
Solution: Review documentation on IAM access controls (compartments and policies). In addition, we suggest using Oracle CASB and Oracle IDCS for further security controls around access policies. For Oracle Container Engine for Kubernetes, our solution is to use Kubernetes Role Based Access Control in addition to IAM.
Look out for a future blog post on Kubernetes security on Oracle Cloud Infrastructure.
Requirement 9: Restrict physical access to cardholder data.
Solution: This is covered under our physical security controls for the datacenter at the availability domain and region level. We have ISO 27001 certification as well as SOC 1, SOC 2 and SOC 3 attestations which provide the basis for control testing relevant to our PCI DSS Attestation of Compliance.
Section 5: Regularly Monitor and Test Networks
Requirement 10: Track and monitor all access to network resources and cardholder data
Requirement 11: Regularly test security systems and processes.
Solution: Use Oracle CASB and Oracle Cloud Infrastructure Audit Services for monitoring. Integrate CASB and Audit Logs with existing SIEM solutions. In addition to this, schedule regular penetration testing of environments based on Oracle Cloud Infrastructure, using the following links: Pen Testing on OCI, Schedule Pen Test via UI.
More telemetry and monitoring features are coming and our teams are working on an automated OpenVAS solution.
Section 6: Maintain an Information Security Policy
Requirement 12: Maintain a policy that addresses information security for all personnel.
Solution: While customers are responsible for their security policies, we are happy to help in anyway we can. Most customers have existing security policies and our team can help with cloud (IaaS, PaaS, or SaaS) specific perspectives. Here is a list of security policy templates per industry vertical from the SANS Institute.
In conclusion, I hope these steps simplify the road to PCI compliance for your environments on Oracle Cloud Infrastructure. Look out for more blogs, white papers, and Infrastructure Security as Code (ISaC) for security and compliance on cloud to ease your migration to Oracle Cloud.
Official Disclaimer: The views and opinions expressed in this blog are those of the author and do not necessarily reflect the official policy or position of Oracle Corporation.
Oracle Cloud Infrastructure services have the PCI DSS Attestation of Compliance. The services covered are Compute, Networking, Load Balancing, Block Volumes, Object Storage, Archive Storage, File Storage, Data Transfer Service, Database, Exadata, Container Engine for Kubernetes, Container Registry, FastConnect, and Governance. In this blog post, we discuss the guidelines that help Oracle Cloud Infrastructure customers achieve PCI compliance for workloads running on Oracle IaaS.
Background
Our guidelines for achieving PCI compliance fall on the shared-responsibility spectrum of the cloud security continuum. The following diagram describes the separation between responsibility for the security "of" the cloud and security "on" the cloud.
As a customer, you are responsible for securing your workloads on Oracle Cloud Infrastructure. In some cases, you need to configure the services that Oracle provides. The responsibility is shared - Oracle maintains the services infrastructure and the customer consumes the services and configures the controls according to their security and compliance requirements. The following picture from the International Information System Security Certification Consortium (ISC2) clarifies the areas of responsibility for IaaS, PaaS, and SaaS:
We follow Oracle's 7 Pillars of Trusted Secure Enterprise Platform to develop solutions that meet the customer’s security and compliance requirements. We will discuss this more in our next blog post on Security Solutions Architecture. For now, let’s focus on PCI on Oracle Cloud Infrastructure.
Recommended High-Level Solutions for PCI Compliance on Oracle Cloud Infrastructure
We follow the latest official publication from PCI Security Standards Council (R) - Requirements and Security Assessment Procedures version 3.2.1 (May 2018). As per the document, there are 12 detailed requirements across 6 sections that cover how to:
Build and Maintain a Secure Network and System
Protect Cardholder Data
Maintain a Vulnerability Management Program
Implement Strong Access Control Measures
Regularly Monitor and Test Networks
Maintain an Information Security Policy
There are additional requirements for shared hosting providers like Oracle and we have already met the requirements through our attestation.
Let's dive into the solutions.
Section 1: Build and Maintain a Secure Network and System
Requirement 1: Install and maintain a firewall configuration to protect cardholder data.
Solution: Use Oracle Cloud Infrastructure security lists (Oracle Cloud Infrastructure managed subnet-specific firewall rules). In addition, download Fortinet or Checkpoint firewall images from our Marketplace and provision firewall appliances on Oracle Cloud Infrastructure.
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters.
Solution: Review the guidance in the PCI document. In addition, we have detailed documentation on how to manage user credentials on Oracle Cloud Infrastructure.
Section 2: Protect Cardholder Data
Requirement 3: Protect stored cardholder data.
Solution: This involves protecting data at rest. By default, Oracle Cloud Infrastructure Block and Object Storage are encrypted. Additionally, with our upcoming KMS, or any supported HSM, Oracle Wallet, Oracle Key Vault and third-party vault offerings, we give you unprecedented flexibility around key and secret management. For data security, we provide Transparent Data Encryption (TDE) and column level encryption.
Requirement 4: Encrypt transmission of cardholder data across open, public networks.
Solution: All our control and management plane communications are protected with TLS, which is necessary for the PCI DSS attestation. We also recommend using TLS (not SSL) and front-ending the application with our load balancers, as and when required. Use of SSH and IPSec VPN along with FastConnect is highly recommended.
Section 3: Maintain a Vulnerability Management Program
Requirement 5: Protect all systems against malware and regularly update antivirus software or programs.
Solution: Use our Dyn Malware Protection service to block malware at the edge of the your logical network before it can infect web applications running on Oracle Cloud Infrastructure. Additionally, ensure that anti-virus software is deployed at the OS level.
Requirement 6: Develop and maintain secure systems and applications.
Solution: We have many recommendations to develop and maintain secure systems. Have a patch management policy in place and use a managed cloud service provider for this purpose. If you're looking for a managed cloud service provider, Oracle Managed Cloud Services is an option along with many of our Oracle Cloud Infrastructure MSP partners.
Section 4: Implement Strong Access Control Measures
Requirement 7: Restrict access to cardholder data by business need-to-know.
Requirement 8: Identify and authenticate access to system components.
Solution: Review documentation on IAM access controls (compartments and policies). In addition, we suggest using Oracle CASB and Oracle IDCS for further security controls around access policies. For Oracle Container Engine for Kubernetes, our solution is to use Kubernetes Role Based Access Control in addition to IAM.
Look out for a future blog post on Kubernetes security on Oracle Cloud Infrastructure.
Requirement 9: Restrict physical access to cardholder data.
Solution: This is covered under our physical security controls for the datacenter at the availability domain and region level. We have ISO 27001 certification as well as SOC 1, SOC 2 and SOC 3 attestations which provide the basis for control testing relevant to our PCI DSS Attestation of Compliance.
Section 5: Regularly Monitor and Test Networks
Requirement 10: Track and monitor all access to network resources and cardholder data
Requirement 11: Regularly test security systems and processes.
Solution: Use Oracle CASB and Oracle Cloud Infrastructure Audit Services for monitoring. Integrate CASB and Audit Logs with existing SIEM solutions. In addition to this, schedule regular penetration testing of environments based on Oracle Cloud Infrastructure, using the following links: Pen Testing on OCI, Schedule Pen Test via UI.
More telemetry and monitoring features are coming and our teams are working on an automated OpenVAS solution.
Section 6: Maintain an Information Security Policy
Requirement 12: Maintain a policy that addresses information security for all personnel.
Solution: While customers are responsible for their security policies, we are happy to help in anyway we can. Most customers have existing security policies and our team can help with cloud (IaaS, PaaS, or SaaS) specific perspectives. Here is a list of security policy templates per industry vertical from the SANS Institute.
In conclusion, I hope these steps simplify the road to PCI compliance for your environments on Oracle Cloud Infrastructure. Look out for more blogs, white papers, and Infrastructure Security as Code (ISaC) for security and compliance on cloud to ease your migration to Oracle Cloud.